Overview
Exploring secure boot mechanisms, trusted hardware, and device protection in transit using hardware roots of trust (HRoT) and BIOS/BMC-level protections.
Research Objectives
- Mitigate firmware tampering during hardware device transit.
- Leverage hardware root of trust for device locking/unlocking.
- Implement secure boot and BIOS/BMC-based device lockdown mechanisms.
- Deploy mesh of trusted agents for secret sharing and device authentication.
Methods
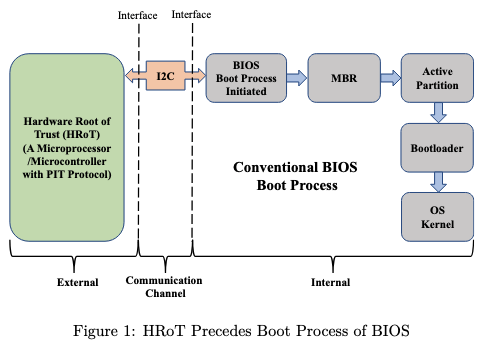
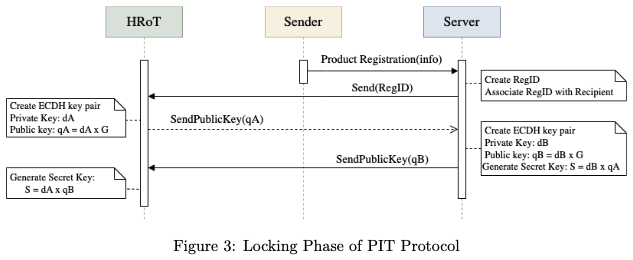
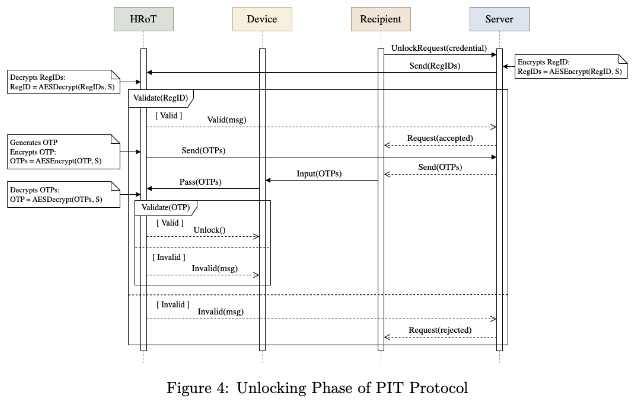
Our project focuses on securing hardware devices in the supply chain. After trusted production, the manufacturer locks the device and ensures that the first use is only by the authorized downstream user. Locking is performed at BIOS/BMC level. Trusted hardware is used to authenticate the rightful user and self-unlock the device securely. Secret sharing between agents ensures robust protection even in complex logistics chains. This work directly enhances trusted computing supply chain resilience.
Results & Visualizations
Impact
Firmware tampering during supply chain transit is a serious risk in modern trusted computing. Even bug-free software cannot operate securely if running on an untrusted device. The BIOS and Firmware Security project addresses this by introducing lock/unlock mechanisms tied to trusted hardware. The protocol guarantees that a device cannot be booted by unauthorized actors once it leaves the vendor. Our approach has direct applicability in military, critical infrastructure, and enterprise settings where firmware security is paramount.