BIOS and Firmware Security
Investigating secure boot mechanisms, trusted hardware, and more...
Read More
S-RFUP: Secure Remote Firmware Update
We present a novel framework (S-RFUP) that integrates industry standard protocols (PLDM, MCTP)...
Read More
AI Planning
We introduce the notion of Attack-Connectivity Graph (ACG) that allows us to perform simultaneous modeling of attack...
Read More
White-box Adversarial Attacks
We conduct a systematic evaluation of various white-box adversarial attacks, where...
Read More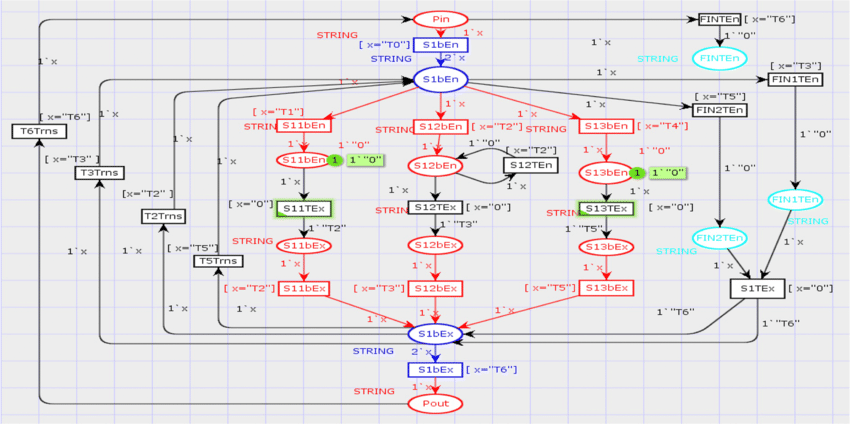
Formal Methods
Enhancing the Protection in Transit (PIT) protocol—which locks devices during transit to prevent unauthorized firmware tampering—we formally verify...
Read More
Resiliency Graphs
We present a novel modeling paradigm, Resiliency Graph (RG) that combines the power of Natural Language Processing (NLP) and AI Planning (PDDL)...
Read More