Overview
We introduce the notion of Attack-Connectivity Graph (ACG) that allows us to perform simultaneous modeling of attack paths and network connectivity. In this formalization, we obviate the need for traditional monotonicity assumptions of attack graphs. We show how ACG can be captured using AI planning models, and we provide complexity results for this process.
Research Objectives
- Develop formal models for Attack-Connectivity Graphs (ACG).
- Map ACG models to scalable AI Planning models.
- Enable interactive human-in-the-loop security hardening.
- Support explanation-driven AI to improve administrator decisions.
Methods
Our approach, called iEXAM, automatically converts network configurations and vulnerability descriptions into planning models expressed in Planning Domain Definition Language (PDDL). This allows us to leverage highly scalable AI planners for various analyses, empowering iEXAM to scale to large networks. The system supports:
- Automated model generation from real-world network data.
- Diverse security hardening strategy identification.
- Human-interactive explanations of AI-generated solutions.
Architecture & Results
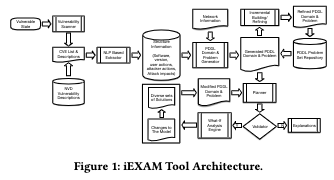
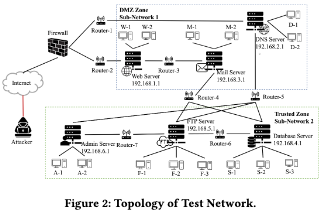
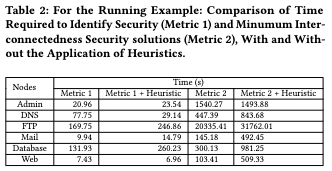
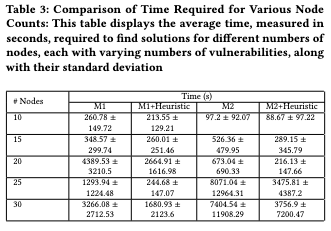
Impact
Attack graphs have been widely used to help cyber defenders understand how networked systems can be attacked and how defenses can be deployed. However, prior approaches rely on complete cost models which are difficult to obtain in large systems. Our iEXAM approach offers:
- AI-driven exploration of security hardening options.
- Explanation-based decision support for administrators.
- Scalable analysis applicable to large enterprise networks.